SSL stands for “Secure Sockets Layer” and refers to a protocol for using the web in a secure, encrypted, manner. Every time you connect to a website with an address prepended with https://, instead of just http://, you’re connecting over SSL. Almost all banks and e-commerce sites, for example, use SSL exclusively.
SSL helps provide security for users in at least two ways. First, it helps keep communication encoded in such a way that only you and the site you are communicating with can read it. The Internet is designed in a way that makes messages susceptible to eavesdropping; SSL helps prevent this. But sending coded messages only offer protection if you trust that the person you are communicating in code with really is who they say they are. For example, if I’m banking, I want to make sure the website I’m using really is my bank’s and not some phisher trying to get my account information. The fact that we’re talking in a secret code will protect me from eavesdroppers but won’t help me if I can’t trust the person I’m talking in code with.
To address this, web browsers come with a list of trusted organizations that verify or vouch for websites. When one of these trusted organizations vouches that a website really is who they say they are, they offer what is called a “certificate” that attests to this fact. A certificate for revealingerrors.com would help users verify that that they really are viewing Revealing Errors, and not some intermediary, impostor, or stand-in. If someone were redirect traffic meant for Revealing Errors to an intermediary, users connecting using SSL would get an error message warning them that the certificate offered is invalid and that something might be awry.
That bit of background provides the first part of this explanation for this error message.
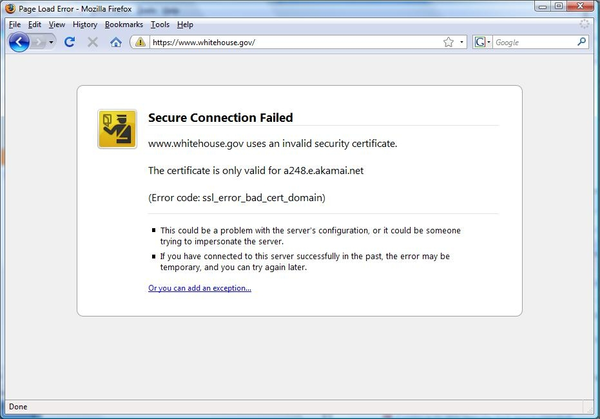
In this image, a user attempted to connect to the Whitehouse.gov website over SSL — visible from the https in the URL bar. Instead of a secure version of the White House website, however, the user saw an error explaining that the certificate attesting to the identity of the website was not from the United States White House, but rather from some other website called a248.e.akamai.net.
This is a revealing error, of course. The SSL system, normally represented by little more than a lock icon in the status bar of a browser, is thrust awkwardly into view. But this particularly revealing error has more to tell. Who is a248.e.akamai.net? Why is their certificate being offered to someone trying to connect to the White House website?
a248.e.akamai.net is the name of a server that belongs to a company called Akamai. Akamai, while unfamiliar to most Internet users, serves between 10 and 20 percent of all web traffic. The company operates a vast network of servers around the world and rents space on these servers to customers who want their websites to work faster. Rather than serving content from their own computers in centralized data centers, Akamai’s customers can distribute content from locations close to every user. When a user goes to, say, Whitehouse.gov, their computer is silently redirected to one of Akamai’s copies of the Whitehouse website. Often, the user will receive the web page much more quickly than if they had connected directly to the Whitehouse servers. And although Akamai’s network delivers more 650 gigabits of data per second around the world, it is almost entirely invisible to the vast majority of its users. Nearly anyone reading this uses Akamai repeatedly throughout the day and never realizes it. Except when Akamai doesn’t work.
Akamai is an invisible Internet intermediary on a massive scale. But because SSL is designed to detect and highlight hidden intermediaries, Akamai has struggled to make SSL work with their service. Although Akamai offers a service designed to let their customers use Akamai’s service with SSL, many customers do not take advantage of this. The result is that SSL remains one place where, through error messages like the one shown above, Akamai’s normally hidden network is thrust into view. An attempt to connect to a popular website over SSL will often reveal Akamai. The White House is hardly the only victim; Microsoft’s Bing search engine launched with an identical SSL error revealing Akamai’s behind-the-scenes role.
Akamai plays an important role as an intermediary for a large chunk of all activity online. Not unlike Google, Akamai has an enormous power to monitor users’ Internet usage and to control or even alter the messages that users send and receive. But while Google is repeatedly — if not often enough — held to the fire by privacy and civil liberties advocates, Akamai is mostly ignored.
We appreciate the power that Google has because they are visible — right there in our URL bar — every time we connect to Google Search, GMail, Google Calendar, or any of Google’s growing stable of services. On the other hand, Akamai’s very existence is hidden and their power is obscured. But Akamai’s role as an intermediary is no less important due its invisibility. Errors provide one opportunity to highlight Akamai’s role and the power they retain.
I’d like to correct a few points of misunderstanding in this post:
– You make the statement “Except when Akamai doesn’t work.” However, in the example you give, the system is working exactly as designed. For customers that choose to deliver their whole site (www.example.com) over Akamai, but choose not to leverage our SSL delivery service, requests for https://www.example.com will cause our servers to return the generic certificate that is used by customers serving only objects securely through Akamai. (As noted, the certificate is for a248.e.akamai.net.)
– For customers that are leveraging Akamai’s services to serve their whole site securely through Akamai, a request for https://www.customer.com/ will, in fact, return a certificate for that hostname. (As an example, do a DIG on http://www.cathaypacific.com, and look at the certificate returned from https://www.cathaypacific.com/. You will see tha that the site is served by Akamai, and that the proper certificate is returned.)
– You note that Akamai has recently begun to offer an SSL delivery service. This statement is inaccurate, as we have offered a Secure Content Delivery service, supporting dedicated customer hostname certificates delivered by a global server deployment, since the 2001/2 timeframe.
Yes.. that “Secure service” you provide.. mitm fits in as expected with 2001 onwards.
Yes, NSA’s big prize might be google, but CIA’s proudest achievement in cyberware is AAkamai.. and it’s not 10-20% it is by your own words, more like 40% of all traffic. That it was released right after 9/11 in 2001 wouldn’t be surprising, although was pretty sure it was before that.
Thanks for the clarifications David.
I’m pretty comfortable with the statement that a big warning certificate from a site the user didn’t think they were connecting to is “not working.” I’m sure it’s a known, even intentional effect, but what constitutes an error or not working can often be subjective. I’m comfortable arguing that the behavior you describe is not what users, or Akamai customers, either want or would expect, and am happy calling that an error.
In regards to your second point, I’m sure that the SSL service works well when clients choose to take advantage of it. I don’t think my post claims otherwise.
Regarding your third point, this definitely is a mistake on my part. I’ll update the text to reflect this. Sorry about that!
Surprisingly even Akamai doesn’t use the SSL delivery service for their Website. https://www.akamai.com/ brings up the same security warning.
I agree with Mako, the Akamai warning message will make no sense to the end user.
(By the way, I just found Revealing Errors through IT’S BROKEN (http://itsbroken.2wtx.com), another interesting blog about things that are broken in life, so I thought I’d leave their link in my comment.)
Off to read your archives!
Thanks, Mako. The relevance of Akamai to privacy, regardless of how well they have SSL working, is an important issue I had overlooked. That’s a nice observation you have there.
-t
@Klaus
That will happen with any site you try to request securely, but isn’t set up to be secure. Why would Akamai use SSL on their public facing website?
@Robert Then why not limit traffic to HTTP only for those domains (which would be fairly easy to do, just have two sets of IP addresses, one with services on 80 and 443 and one with only 80).
I am not understanding whether I am suppose to “proceed anyway” when I get this error message? The last thing I need is a virus – so I am a little leary.
I receive this message using Google Chrome as my browser, Windows XP as my operating system, and I am only trying to get onto Facebook. I am in social media marketing so it is imperative that I understand this.
Any help or advice I would be grateful for.
Absolutely not Barb! Your problem however, is that your ISP has allowed Akamai to act as an ssl attacker… You can ban the proxy ip’s and then conplain and insist on working internet (they will convince you about this is fair play, which it is not).. but in the end, I doubt you will win through. It would take a mass lawsuit from your ISP’s users to win through. If you live in a free country, as far as it goes, you should do well there.
I am not understanding whether I am suppose to “proceed anyway” when I get this error message? The last thing I need is a virus – so I am a little leary.
I receive this message using Google Chrome as my browser, Windows XP as my operating system, and I am only trying to get onto Facebook. I am in social media marketing so it is imperative that I understand this.
Any help or advice I would be grateful for.
Just a note:
SSL hasn’t really been used or supported since 01/1999. It’s called TLS (Transport Layer Security) now, since the publication of RFC 2246. The prior specification, SSL 3.0, was never actually a full specification, just a collection of “if we do this, things generally don’t break” ideas.
Most places still have SSL fallback turned on, and until Windows Vista Microsoft made IE not use TLS by default. I don’t know why, since SSL 3.0 relies on the security of MD5 while TLS relies on the higher of security between MD5 and SHA1. (There are newer versions of TLS which will support even more MAC hash algorithms.)
Other than that, though, I feel you’re right on the money. That’s one of the worst possible error pages to show — and the worst thing is, it’s part of the user’s browser. It’s not anything that the site can control, other than adhering precisely to the demands of the browser.
wtf is going on someone please tell me did I install malware on my computer that wants to steal my login information this is reallly irritating me as I just want to long in to netflix, facebook, my BANK I don’t want akkkslomi to have my bank login information someone please what is going on how do I take this virus off my computer and how do I make assholami doesn’t have my bank information!!!!!!!! THIS IS SERIOUSLY PISSING ME THE FUCK OFF
Lol.
Haha. I just laughed so hard. Security and privacy after using facebook. I can’t breathe. I think I peed a little.
It’s really interesting that Akamari is a legitamate business, and most internet users utilize it every day, but I think a lot of us are more interested in hearing a solution to the problem we keep having, and so far it seems like no one can supply that. When Akamari isn’t working, or I guess you could say “working visibly”, and is stopping users from accessing the internet recources they would like to be accessing, how can the user continue to access these sites? Is there a solution? If not I would say some one (Akamari?) has a serious problem they need to address.
Great, so now how about giving some information about how we should deal with the problem when it occurs..
How can we fix it and or get around it?
A solution, For anyone whos having an Akamai or Invalid URL message on facebook, repair your router, either switch it off or repair it (by clicking the repair button) and your issues will be resolved!, spent an hour researching until i found the answer that resolved my problem..
Hope this helps
cheers
– Ash
I think the Facebook issue (and whitehouse.gov issue, presumably) is a server-side issue for most people, and there’s a couple of reasons why it is a massive job to fix:
1) It is region-specific, so the developers located in California won’t see the issues in Italy, South Africa or Australia.
2) It involves their partner site Akamai.
3) It is a site wide issue, which involves possibly altering DNS settings etc., so it probably can’t be resolved without serious amounts of paperwork and organisational double-checking.
Having said that, in the affected areas (I have heard Italy, India, South Africa, and Australia) the Facebook API authentication is completely broken short of users clicking the ‘proceed despite the risks’ button in their browser, which is discouraging. I hope they fix it soon.
Matt
If I hit ‘proceed’, will I have an unsecured or unsafe connection? Problem occurs in all browsers when attempting to connect with facebook.
None of this covers why Akamai feels the need to persistantly portscan anything and everything that connects to a site hosted on one of their servers, and their own website fails to explain the need for this assault.
Marko I have only one question! I have bunch of application enabled SSL within. So should I go with Akamai and does it really works well with SSL?
This problem happened to me when trying to sign on to Facebook using Chrome on a Windows XP machine. It is true that the error message gives you the strong impression that your system has been hijacked. I did virus and spyware scans and doublechecked the traffic through my firewall with no errors. Following a tip from one of the posts here, I repowered my cable modem and router and that seemed to take care of it.
I feel a lot better now.
Not happy about this Akamai shit. Have spent ages looking into DNS redirecting and am convinced there is a connection here with Akamaitechnologies. What do we do, stop purchasing stuff online because that is the only way to be secure? Very worrying indeed. The Internet is rapidly becoming an unworkable pool of shit. God only know what it will be like in ten years time??? When I have found a way to block Akamai, I will and if that means I can’t access sites as a result then so be it!
Christopher, Linger in the Darkness, or Join Us….Join Us…Join Us…..
How to fix this a248.e.akamai.net:
1) Follow instruction above by Hybrid24. This works a attested by GK Mandigo.
On a side note, I did not specifically power cycled or restarted or refreshed my router since it is quite far from our room. What I did was:
Access your router set up(192.168.x.x) and disconnect & reconnect your internet connection on the internet connection status subpage.
My router is Cisco v3.0.0.02
Our internet connection type is PPPoE.
1. Open your router set-up. for cisco linksys, this could be accessed through 192.168.1.1 or through network magic(i don’t know how though).
2. Go to STATUS PAGE.
3. On the Internet connection details portion, there is a “Login Status” indicating that you are connected and on the side, there is a “disconnect” button. Press the button and when the numbers are set to “0”, Press the “Connect” button.
4. Try facebook again. This should fix your problem without the added hassle of moving around.
^__^
I hope this helps anyone.
Oh dear god. You idiots.
Look no ones hacking anything, Akamai are major part of internet infrastructure that a lot of people rely on.
If you go to a site via https and get an error explaining that blah.akamai.com isnt a valid host its because the site yout trying to go to, doesnt intend for you to access their site via https.
So stop ranting and trying to block the internet.
Well said! Whew…
I do receive Certificate Warnings at different times; options given: View certificate; Go back; Proceed.
I was trying to hook up with Yahoo to finish a news bit.
Decided to View Certificate & look see. I read along your comments & do for the most part “get it” & I am sure it is all an encompassing power house to be certian, but many are & will continue to question these certificates, I do understand this as well being a just an End User, but this could be avoided/tweeked I feel sure. I have not a clue, will leave that to you “big dogs”.
Thank you, Deb.
problem in SSL
that address belongs to a girl using google webmaster tools to ride akamai technology with a reinvented name using their meta tags she has been bragging to her friends on google webmaster that she has taken over facebook putting access denail codes into your application modules…she is operating out of LA somewhere, no techs working with atamai technology have addresses on the web wake up fools
17th Jan 2012 .14:16.
….. and now they tell us just as we are in ‘banking scary season’ again and we have this to worry about is it any wonder we are all being bombarded by some Oik from one bank or another trying to tie us all up for 2 years in an e-bond, they get the 18% whilst they can and we end up with the falling brick.And why do I mention it because of the eTrade email scam thats going about and not knowing how they are getting the addresses and the amounts so right,so of course lets nick the info on file and we will merge it with a non cert remailer who will in the end get nothing but free publicity from this connection.
Not pertinent you say!Look at the amount of people who spent good money last year on an external CD player because they could not get rid of the redirect script in the temp file for the driver add on that if you knew how you could do it yourself and could clear the error in an instant otherwise just when you need sound on your device someone come’s up with a site that has no cert that automatically kicks in the script which appears to be trying to protect me and you online yet doing the exact opposite.
J Clarkson is right again…..in front of their families..
None of this covers why Akamai feels the need to persistantly portscan anything and everything that connects to a site hosted on one of their servers, and their own website fails to explain the need for this assault.
This “explanation” sounds to this journalist like a military contractor psyops cover story to camouflage a covert government censorship regime that routinely and warrantlessly intercepts, edits and maliciously alters content received by so-called “targeted individuals” — which could be anyone that someone in power wants to neutralize, for any reason, usually based on ideology or hate. Read this:
http://viclivingston.blogspot.com/2012/03/us-cyber-censorship-regime-fakes.html
I am interested in hearing an explanation for this, which appears to be being ignored?
“None of this covers why Akamai feels the need to persistantly portscan anything and everything that connects to a site hosted on one of their servers, and their own website fails to explain the need for this assault.”
There are threads on the Internet going back to 2004 and probably earlier where this nonsensical issue hasn’t been explained. The Akamai rep’s explanation doesn’t make sense because this error pops up on apple.com’s internal links. Simply navigating through a website shouldn’t be bringing up SSL errors.
https://apple.com is certified by Akamai SSL CA’s apple.com SSL certificate.
http://i.imgur.com/N62Qs.png
Trying to download from that page brings the error stating an “attempt to reach images.apple.com instead reached a server a248.e.akamai.net – you should not proceed” etc.
http://i.imgur.com/oMwKc.png
Doing the same thing from http://apple.com goes straight to the http page (images.apple.com) and allows the download without an error message.
http://i.imgur.com/4K0ej.png
If you ignore the warning you can then proceed to https://images.apple.com which is verified by Akamai’s http://www.apple.com CA.
http://i.imgur.com/9MMEp.png
However, going to https://images.apple.com directly gives you a warning message and shows that it’s incorrectly verified by Akamai’s CA and NOT Apple’s.
http://i.imgur.com/cUH2O.png
Now I’m slightly dizzy and confused but it seems to me yall at Akamai can’t seem to get your links and certificates straight; for almost two decades now.
If this is in fact correct, how are you convincing all these multi-billion $ corporations to host their sites on your servers?
I started criticising political corruption, and have had 14 months of crashing systems and corrupted Root CAs and certificate errors and Denial of Service. This is something that continually pops up with other posters saying they started criticising politicians and suddenly, they have Akamai certificate problems.
Is your company corrupt? Or merely incompetent? Pretty sure the major web browsers are all corrupt, so forgive me if it’s just trendy or something.
Why would anyone want to enter any site that states: “Invalid Security Certificate”!!! I have received hundred of these from akamai…and some even say “staging”! There are many other “Invalid Certificates” on my computer and currently I cannot sign in to sites on the internet. If Akamai is a “Valid” Certificate then you should say that it is and why it pops up! I think others “who are truly cybercriminials” are using your certificate as well. What a surprise to read that these certificates even pop up when trying to reach http://www.whitehouse.gov. If you are legit, you should state it!!
Great information. Concise and to the point with examples, unlike other sites that devolve into meaningless side comments! I finally understand why I get the FF warnings about untrusted networks.
Thanks.
I just found this article — ironically, I tried changing the URL of this page to use HTTPS (https://revealingerrors.com/akamai_ssl) and I got a big red security error! (I’m using Chrome, and this site is using a self-signed certificate.)
By the author’s definition of an error (in their comment responding to Akamai’s response), “the behavior … is not what users … either want or would expect, and am happy calling that an error”, this is clearly an error.
How to get conntent like broken URL information from Akamai server
I loved as much as you’ll receive carried out right here. The sketch is attractive, your authored subject matter stylish. nonetheless, you command get got an impatience over that you wish be delivering the following. unwell unquestionably come more formerly again since exactly the same nearly very often inside case you shield this hike.
t-huh?
The real problems are these: Akamai addresses are treated as impostors by my Chrome browser though I have never configured settings to reject akamai addresses. Therefore, the use of akamai on my machine in tantamount to a denial of service, since Chrome refuses to let me go there with the explanation that security settings are too high to proceed. Secondly, the question of whether or not one is connecting to a “public face” http or https is silly for an end user who is used to creating Bookmarks on the fly, regardless of whether the page being bookmarked is an http or https address. One is as likely to be recalling an https page as an http in the real world and they simply have to be handled properly and politely by the SW in use.
You guys need to calm down. I have a question, so someone said that Akamai can take messages and or change them or distort information because they are not held by any laws and most of their work is underground so people wouldnt know about it anyway. Is this true? I’m not bashing Akamai or anything, i’m just curious. Also I am on a screen reader. It doesn’t have any major settings. So how on earth do I get the warning off when i’m logging onto something???? My javacript always warns me abot Akamai before I’m about to log into facebook, how do I make it stop?
Hi Ashwani!
I have no idea about the specific details of this. You should talk to Akamai about this. They should be able to tell you the limitations of their systems.
It’s been a long time since I’ve ready so much FUD on a topic. Akamai returning certificate errors when the customer didn’t pay for Akamai’s SSL service is not only NOT an error, but entirely expected. What looks like an error from a user perspective is just WAD (works as designed) from a server perspective.
Saying things like “why can’t it direct http and https traffic to different servers?” betrays a gross lack of knowledge of how the internet works… a DNS lookup for a hostname / IP address isn’t going to differentiate based on the protocol. Sure, there are SRV records but that’s not what’s used when resolving an IP.
Since SSL works by only allowing one endpoint certificate per IP address, customers who need it have to pay extra because IP addresses are in short supply, and SSL also increases operating costs for the extra CPU load.
On the security side, no website can be FORCED to use Akamai, so it’s a business decision by the operator of the website whether to use Akamai’s services or not. If my bank wants to accelerate their site through Akamai caching, that’s my bank’s decision. Yes, Akamai technically acts as a “man in the middle”, but it’s by design. Akamai configurations allow for traffic to be pulled from the origin server securely and then passed from Akamai to the last-mile securely, with no decryption possible in the middle/Akamai layer. So again, it’s up to the operator of the website (a bank, CC processor, etc) to set it up that way so that there’s no plain-text cache of data anywhere else.
So avoid the conspiracy theories, learn more about how Akamai actually works, what it does, and just some fundamentals about how the internet works, before spreading rumors.
I know how Akamai works and I know how DNS works. I have friends who work at Akamai and, if you read carefully, you’ll see that people at Akamai have commented on this article and that I’ve made changes based on that feedback.
The big scray error message is in the screenshot from a site that a user did not know they were visiting is an error. The fact that Akamai — and perhaps even their customers — knew this was going to happen does not make this desirable or expected behavior for the users or, frankly, for anybody else involved. This is a limitation of the way that Akamai and the technologies it uses (like DNS) works in the ways you have described. But the fact that limitations are systematic does not mean they are not errors in the way that I use the term on this site.
I did not say that they could just redirect HTTP and HTTPS traffic to different sites, so I do not know why you are accusing me of being ignorant for doing so.
So why don’t Akamai use their own Secure Content Delivery service for https://www.akamai.com rather than returning a certificate error ?
As there is no need serve Akamai public website over SSL they wisely redirected all https://www.akamai.com requests to http://www.akamai.com . Why consume resources if there is no need to.
It’s now 2013 and I still get the cert warning when visiting http://www.bing.com
I don’t see how anyone could use them on a regular basis unless they Never clear their cache.
You probably always will. I don’t see any reason why they’d by an SSL Certificate, and apparently neither do they.
While proxy cache’s to increase the apparent speed of internet use sounds appealing, this seems like it is a potentially malicious implementation. What if I want to connect directly to WhiteHouse.gov, not some DNS-spoofing-SUXNET worms version of the internet– including a nice little silencing of any complaints. Especially when software is involved: I connect to my ISP, whose IT guy downloaded some binary in the server stack who then directs their clients to install a similar version of the worm (using DNS spoofing). What if when I purchase something on Amazon, this tactic is employed to coerce me into purchasing at an increased price or through an intermediary. Or perhaps a state Government utilizes this to sway public opinion or silence other state’s outrage at state’s actions. Even worse a terrorist entity cripples the communication lines in a strategic compromising blow.
These may be the worried thoughts of one who ponders things too deeply, but it all seems very possible and likely eventually. Wish the NSA was doing something about this, instead of it’s campaign to reduce funding (those are those guys who listen to my phone calls, right?). After trying to download some sorcecode from a government entity who failed to allow https connections (and resolved an IP I’m fairly sure was a local subnet) it makes me wonder, what’s going on here– and how bad is it.
BTW, such a proxy cache can have it’s cake and eat it too– use the original certificate to fetch a checksum (ssl) and if it compares same to the nearby copy fetch the nearby copy instead. Then, the browser, can send the checksum of the cache retrieval and send it back to the original site. Anything else, in regards to this practice, just seems like a way to insert/replace ads, send money order payment orders to amazon while the original order is charged to some off-shore hoax, flood in net with malware, or some kind of even-more-terrorist activity.
All of this is way to complicated for an ordinary user to consider, or even be asked to do so, so why isn’t the NSA fixing this– it should be pretty easy(well for them…) to do if you have access to lots of logs.
Akamai is a SSL mitm attack by US govt. It doesn’t need to be, in the meantime it also acts as a ‘transparent proxy’. The problem is, NSA has CA root certifictes at will etc, so with Akamai, you can be sure none of your encrypted traffic is really safe.
Until proper open protocols are put forward internationally, countering US corporate and military injection and subterfuge, there ain’t a whole lot one can do.
I see comments which actually refer to the MITM attack by NSA/Akamai, are removed here… leaving just the silly rants. Not trustable site, as so many.
I haven’t removed any comments except spam comments. All comments are moderated and I have been way behind on approving comments, however.
Thanks for this Website, i laughed so hard :-)
“I’m trying to get in your house, through your garage, but i can’t. That is an error!”
“I don’ have a garage!?”
‘I know you don’t have a garage, but still i can’t get in your houese through it. That is an error!”
Akamai are too hopeless to be able to silently redirect you back to the original secure site when requested if the company doesn’t have an ssl subscription
Akamai is Big Brother.
Not a day goes by that a248.e.akamai.net does not mess up my internet activities. They are perpetually parked at my website, scaring away viewers of my photography and any ability to make a sale. They were reported as logging into my Facebook account. Privacy warning message run throughout the internet. If your site has one of their privacy warnings attatched to it, your site is ruined. Even your best friend won’t risk sacrificing their computer, on the hope that they will not obtain a virus by visiting it. What is needed is a class action suit against them!
If I bring up this page via https, I get a similar error from a different provider:
This server could not prove that it is revealingerrors.com; its security certificate is from communitydata.cc. This may be caused by a misconfiguration or an attacker intercepting your connection.
Ironic? Should everyone be worried about communitydata.cc “intercepting” the content they are hosting for revealingerrors?